BSides RDU
10th Anniversary!
Friday, September 22, 2023

Check out our Linktree to follow us on
All The Socials!  for News and Announcements!
for News and Announcements!

Sponsors
Call for 2023 Sponsors Remains Open!
There still are many sponsorship opportunities!
Sign up as a sponsor today!
For more information or questions about sponsorship, please contact
events (plural)
at BSidesRDU
dot org.
The Venue
Please note: We are at a new venue this year!
The McKimmon Conference and Training Center at NC State (MCTC)
Floor Plan
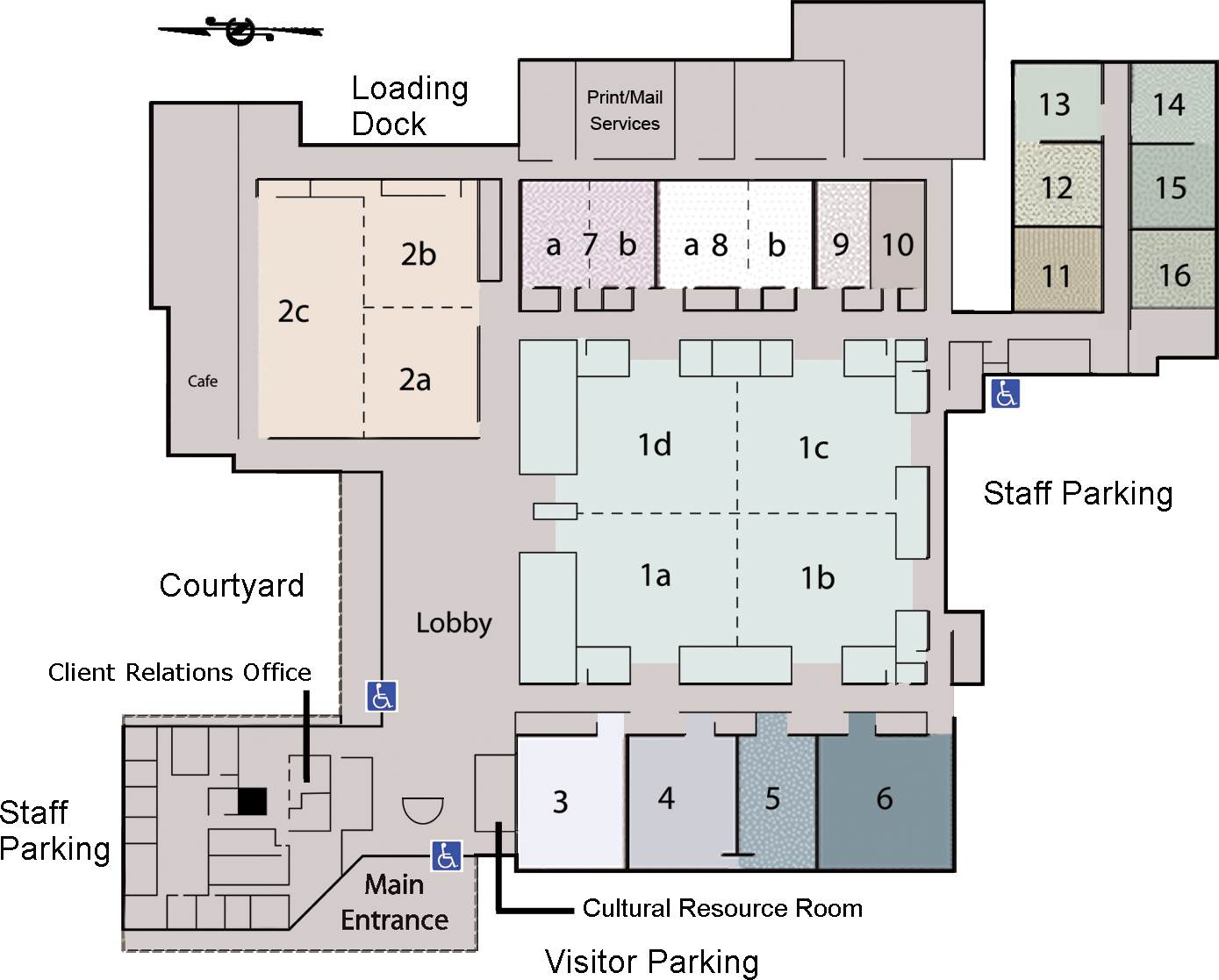
Note: Floor plan is oriented 90 ° counter-clockwise. That is, North is on the left side.
Parking
Parking is provided Free at the Mckimmon center.
After Party 🎉
Location: Raleigh Brewing Neil St (3709 Neil St, Raleigh) Taproom
Event Time: 6:00pm – 9:00pm
Catering:
Ruckus Pizza. Pasta, sushi, chicken tenders.
Plus there will be Gluten Free, Vegetarian, and Vegan options.
Speakers
About
Security BSides is a community-driven framework for building events for and by cyber security community members. The goal is to expand the spectrum of conversation beyond the traditional confines of space and time. It creates opportunities for individuals to both present and participate in an intimate atmosphere that encourages collaboration. It is an intense event with discussions, demos, and interaction from participants. It is where conversations for the next-big-thing are happening.
Security is top of mind across the entire sphere of IT and the world beyond. Therefore, more people and organizations are interested in the next new thing in security. BSides is the place where these people come to collaborate, learn and share.
With many tech-companies, colleges and universities in Raleigh, Durham, Chapel Hill and surrounding areas, it is also an international center of innovation in the security industry.
Security B-Sides Raleigh-Durham (B-Sides RDU) is proud to have had great speaker lineups at our events including keynotes by Dan Kaminsky, Dave Kennedy, Paul Vixie, BenTen, Jay Beale, G.Mark Hardy, Cliff Stoll, Shahid Buttar, Chris Wysopal and Bruce Potter.
Principles
We don't think this should be too complicated. Conduct of all who participate in our community should be based on open dialog, a willingness to learn, and helping each other out. For Security BSidesRDU, our rules of conduct, principles, and values are listed here.
1 Conduct
We believe that there are simple rules for governance at any meeting of people striving to be a community:
- Don't be an asshole.
- Be willing to learn.
- Be willing to share.
- Be willing to help.
- Be willing to listen.
- Accept criticism.
- Be kind.
BSidesRDU is not an elementary school. It’s not a land full of rainbows and unicorns. Neither is it hell on earth. If you believe someone is misbehaving, acting inappropriately, or acting illegally, start by talking to that person. Confirm your perspective. If you are unable, or unwilling, to do that, that’s OK -- find a BSidesRDU Staff member and talk to them.
2 Principles
Security BSides operates under three simple principles:
- Expand the conversation.
- Enable people to join the discussion.
- Get people involved.
BSidesRDU supports those principles as part of our regional BSides operation. What that means is that BSidesRDU is your conference. It is up to everyone involved to make it happen, to engage in the debates, to speak up and give voice to the issues. Feedback to the organizers is always welcome.
3 Values
Each BSides is a community-driven framework for building events for, and by, information security professionals. The goal is to expand the spectrum of conversation beyond the traditional confines of space and time. BSides creates opportunities for individuals to both present and participate in an intimate atmosphere that encourages collaboration. It is an intense event with discussions, demos, and interaction from participants. It is where conversations for the next big thing are happening.
We value
- We lower the barriers for people to participate.
- We involve people in organizing the events, to help them participate, involve a diversity of input, and teach a new generation of organizers.
- We build and use tools that enable greater participation, share ideas, and enable others to share the magic we collectively create. We share our work openly.
- We help grow the community, because a stronger group helps everyone involved.
We participate
- There are no bystanders.
- We all participate in different ways, including: audience, speakers, organizers, sponsors, volunteers.
- We encourage everyone to share their skills, expertise, and talent.
We steward
- We make decisions that strengthen the brand for everyone, not just ourselves.
- We remember that we are not owners of the brand, or the event, but simply caretakers that carry the torch for a period of time, until we - pass it to others.
- We treat others with grace and respect at all times.
This work is licensed under a Creative Commons Attribution-NonCommercial 3.0 Unported License.









